Hypha members weigh in on proxy battles and the importance of local-first networks
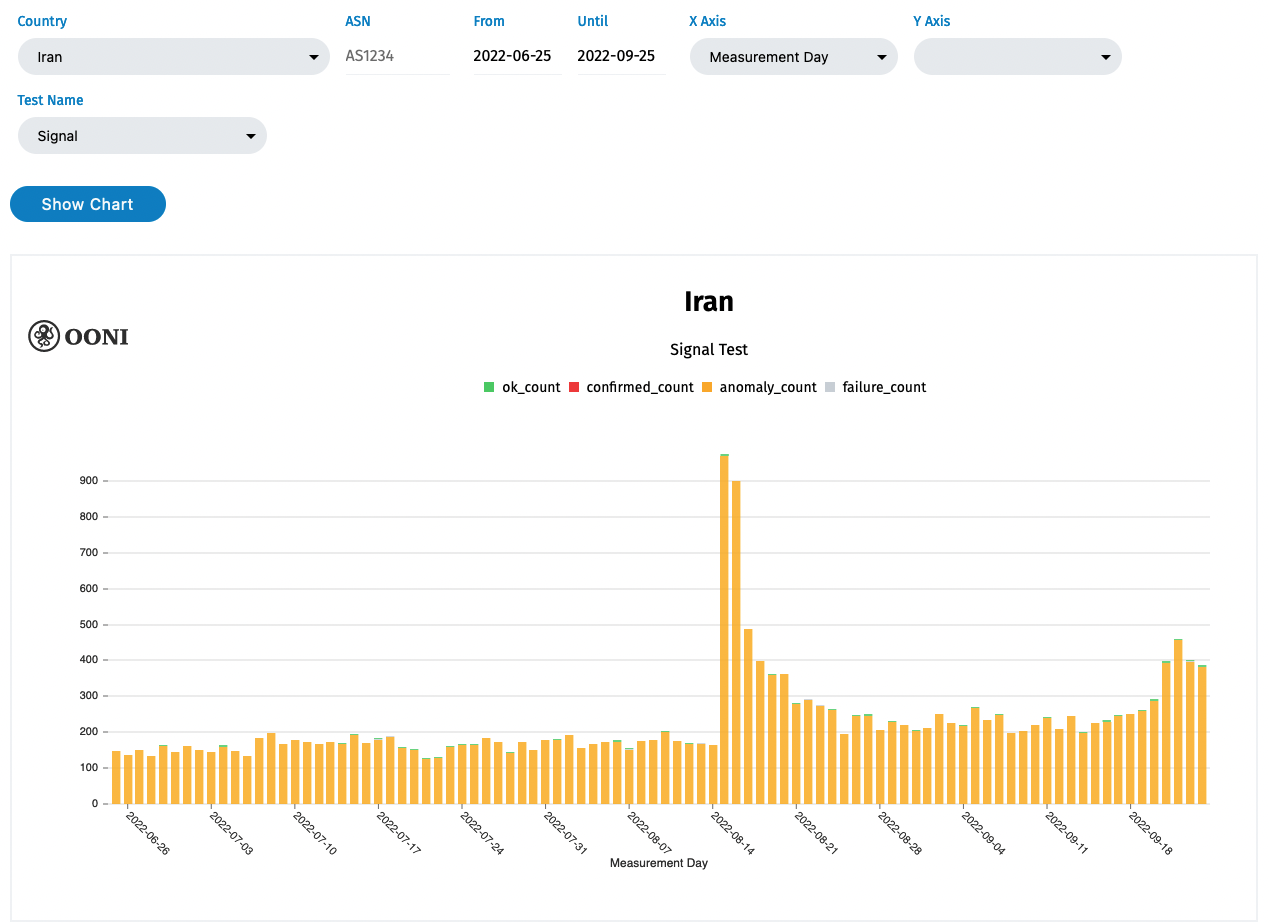
On September 13th 2022, Mahsa Amini was killed in police custody in Iran; since then, protests over her violent and unjust death have spread across the country. Iranian authorities have responded by shooting and killing peaceful protestors and by cutting off Internet access. Last week, Signal, an app well-known for its solid privacy features, put out a call to its community asking for people to run proxies to help people in Iran connect with the app and thus each other.
Hypha members saw the call and spun up several proxies, alongside hundreds of others who rapidly responded over the weekend. Twitter was quickly swamped with Signal proxy announcements, either publicly posted or privately shared over Twitter DMs. We quickly realized that this would be the beginning of the proxy battle, where the Iranian government races to block the discovery and availability of proxies in their region, as new ones are spun up and their access information trickles into the hands of those who need it.
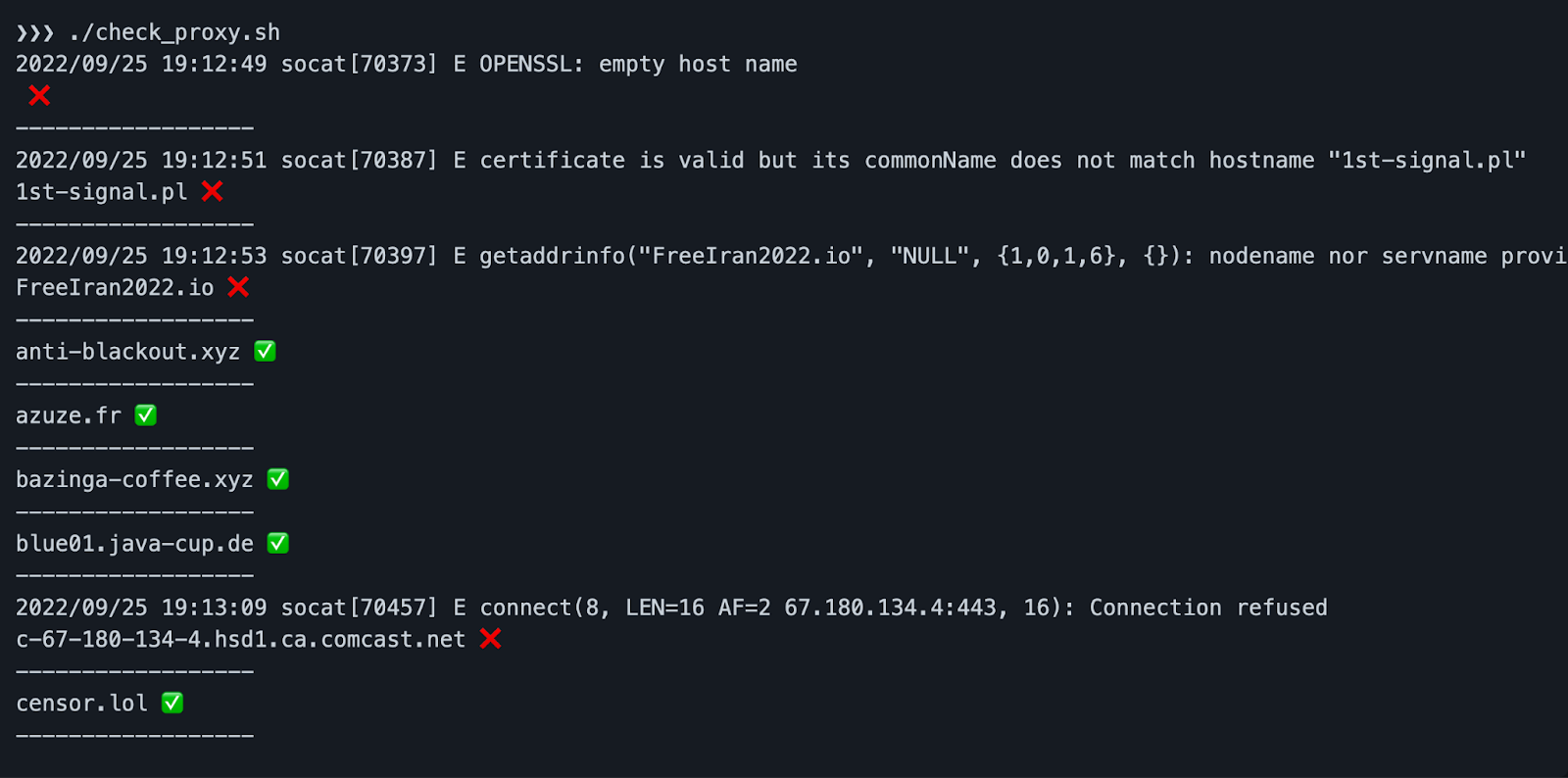
Over time, many of these proxies will become unavailable, either because they’ll have their IP addresses blocked by the Iranian government or due to general lack of maintenance. While it may seem a good idea to post a centralized list with current status, this would only aid the censors in easily identifying which IP addresses to block. Therefore, we figured the best thing to do was to publish the code to check a list of proxies for functionality. Our hope is that these will be used by folks inside Iran so they can rapidly qualify private lists of Signal proxies that are functional inside the region, and then ration them out via trusted human networks.
In situations of protest and the resulting Internet censorship and shutdowns, it’s often challenging to understand and think through on-the-ground needs of the people affected. Simpler solutions are frequently embraced, which although important, obscure the need to build longer-term and more resilient network infrastructure. For example, people in Iran are not able to sign up for new accounts on Signal because the standard sign-up process includes receiving a verification code via SMS, which isn’t feasible for many right now. Therefore, simply stopping SMS messages, or blocking Twitter, become effective ways to control the prevalence of Signal usage.
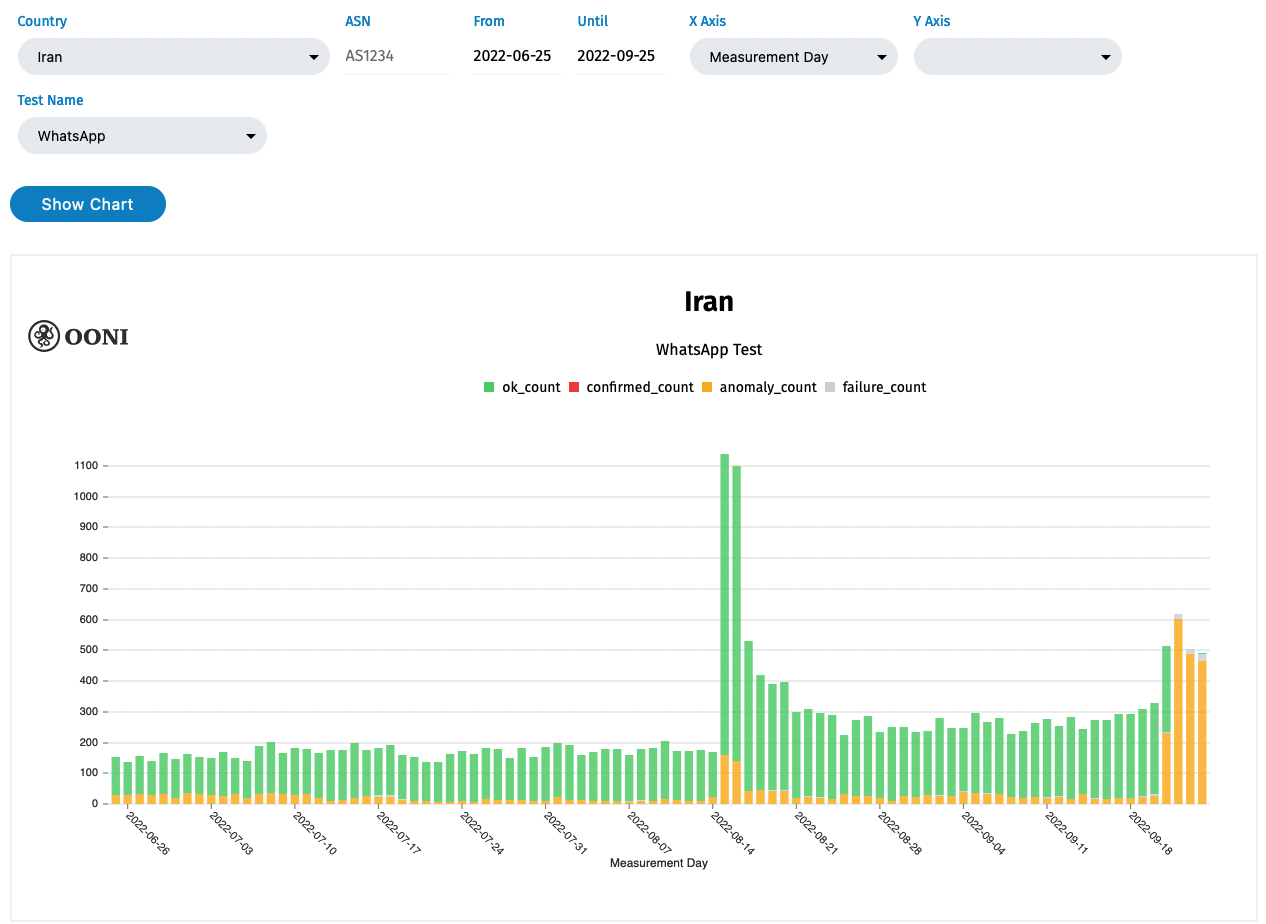
If the Iranian government shuts down Internet traffic altogether, none of the Signal proxies will work as the Iranian network “splinters” from the global Internet. This requires self-healing network protocols that are local-first and capable of converging quickly on network splits. Network experiments like cjdns and Yggdrasil have these properties, and applications like Briar Project and SSB (Secure Scuttlebutt)-based Manyverse and Planetary are likely to work better in splinternet environments.
The proxy checking code is just a starting point, aiming to provide support as the situation in Iran unfolds. We welcome suggestions on how to extend this work to make it more useful in the region, and encourage organizations who are based in Iran to reach out if they have suggestions for local agencies to work with to build private trustful networks.